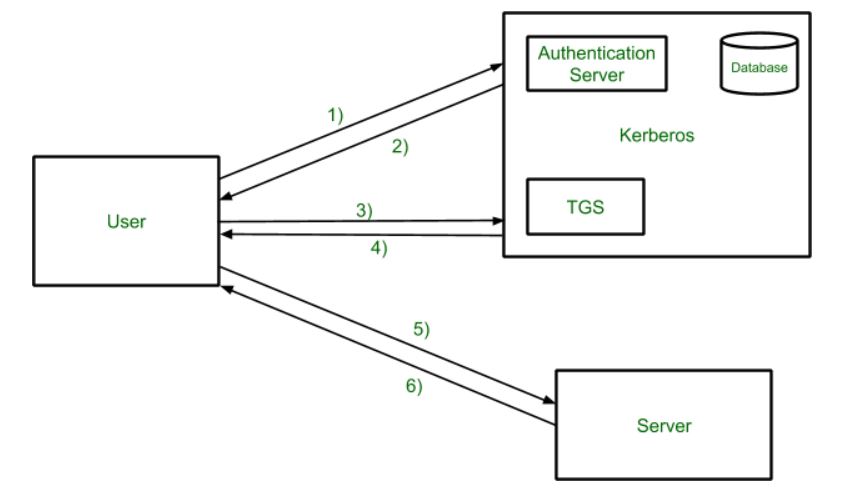
Kerberos / The Original Kerberos Authentication Protocol Phase 1 Client Verifies Download Scientific Diagram
Kerberos maison dédition suédoise. Kerberos protocol a computer network authentication protocol to allow server communication over a non-secure network.

Kerberos Tickets Vulnerabilities And Solutions Optiv
Kerberos Productions studio de développement de jeux vidéo.

Kerberos. La version 5 du protocole Kerberos a été normalisée par lIETF dans les RFC 1510 septembre 1993 et. It is designed to provide strong authentication for clientserver applications by using secret-key cryptography. Kerberos is adopted by a huge number of industries so any new weaknesses in its security protocol or in underlying modules are quickly corrected.
The Authentication Server performs the initial authentication and ticket for Ticket Granting Service. Kerberos tickets represent the clients network credentials. Kerberos is available in many commercial products as well.
Kerberos is a network authentication protocol. Kerberos 简单来说就是一个用于安全认证第三方协议它采用了传统的共享密钥的方式实现了在网络环境不一定保证安全的环境下client 和 server 之间的通信适用于 clientserver 模型由 MIT 开发和实现. The main components of Kerberos are.
The weakest link in the Kerberos chain is the password. Kerberos signifie Cerbère en grec. Kerberos Dante a character from Saint Seiya.
Kerberos moon a moon of Pluto. Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network like the internet. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials.
Each user and service on the network is a principal. With SSO you prove your identity once to Kerberos and then Kerberos passes your TGT to other services or machines as proof of your identity. Un article de Wikipédia lencyclopédie libre.
Kerberos runs as a third-party trusted server known as the Key Distribution Center KDC. Kerberos excels at Single-Sign-On SSO which makes it much more usable in a modern internet based and connected workplace. Le protocole Kerberos est issu du projet Athena du MIT mené par Miller et Neuman.
Kerberos protocole informatique dauthentification réseau. It uses secret-key cryptography and a trusted third party for authenticating client. Kerberos authentication supports a delegation mechanism that enables a service to act on behalf of its client when connecting to other services.
Krematorium Kerberos od svého počátku mělo cíl poskytovat kremační služby důstojným a příjemným způsobem. The Kerberos protocol defines how clients interact with a network authentication service. Klademe důraz na trpělivou komunikaci s majiteli zemřelých zvířat protože si uvědomujeme bolest kterou každý prožívá když mu jeho mazlíček umře.
To streamline these microservices we have implemented Kerberos Hub queue. Clients obtain tickets from the Kerberos Key Distribution Center KDC and they present these tickets to servers when connections are established. Kerberos Productions a game development studio.
The weaknesses of Kerberos are. This queue which relies on Kafka allows our customers to scale have high availability in place and most importantly implement custom code and functions. Kerberos mythology or Cerberus the hound of Hades.
The Kerberos Hub comes with a bunch of microservices for pre and post processing the recordings. If a non-authorized user has access to the Key Distribution Center. Kerberos may refer to.
Kerberos un genre éteint de grands mammifères carnivores. Kerberos 是一种身份认证协议被广泛运用在大数据生态中甚至可以说是大数据身份认证的事实标准本文将详细说明 Kerberos 原理PS. A free implementation of this protocol is available from the Massachusetts Institute of Technology.
这是 Introduction To Kerberos 的文字版感兴趣的小伙伴可以直接. Kerberos 服务是 单点登录 系统这意味着您对于每个会话. Ce nom peut aussi désigner.

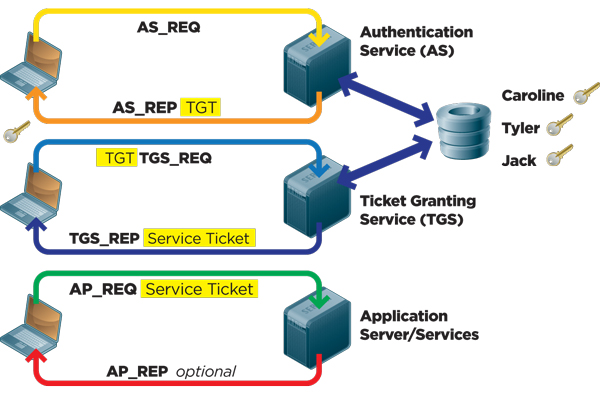
How Kerberos Authentication Works

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram
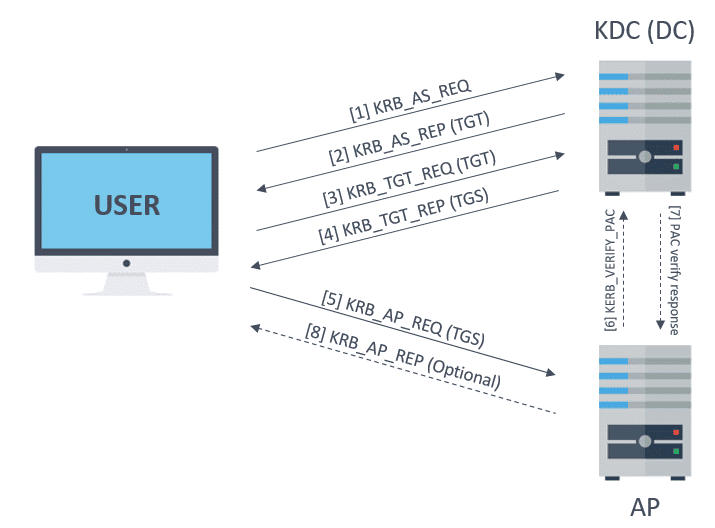
Kerberos I How Does Kerberos Work Theory
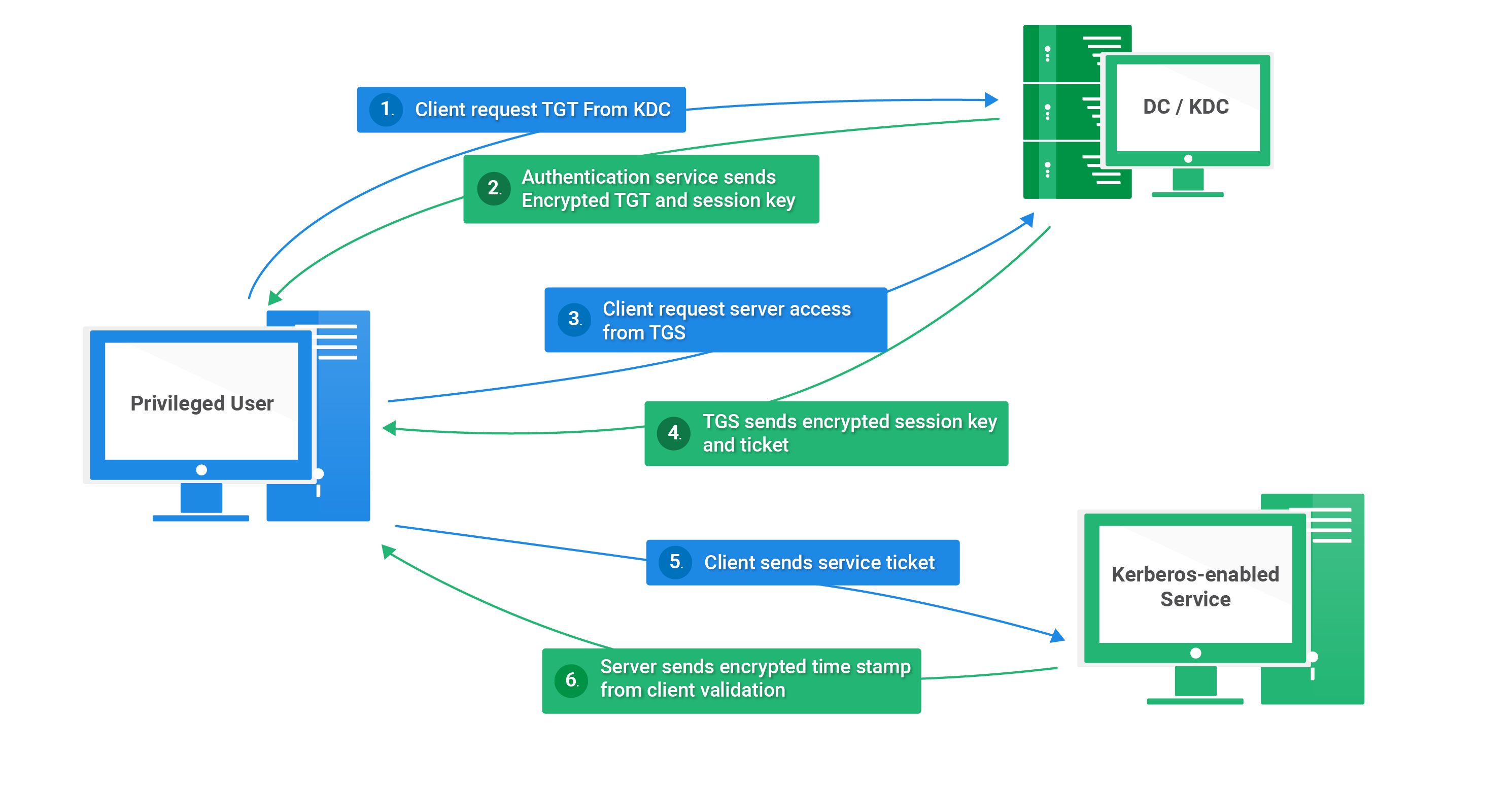
Kerberos Fundamentals What It Is And How It Works Qomplx
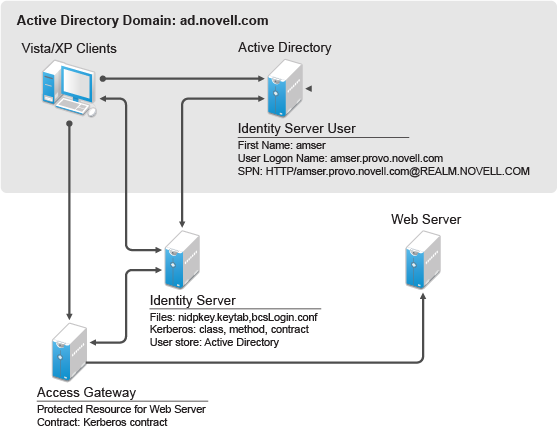
Kerberos Authentication Netiq Access Manager Appliance 4 5 Administration Guide

Taming The Beast Kerberos For The Sql Server Dba Youtube
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com
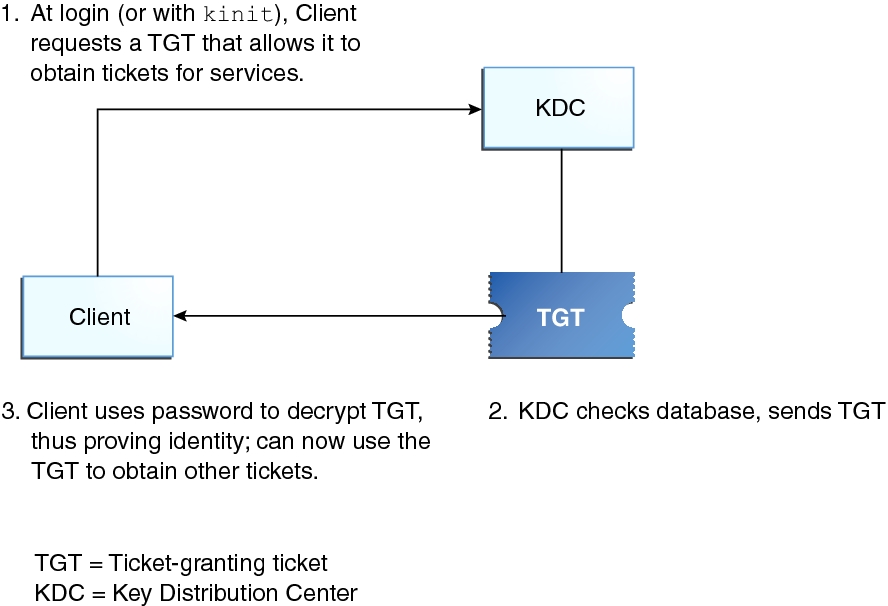
How The Kerberos Service Works Managing Kerberos And Other Authentication Services In Oracle Solaris 11 3
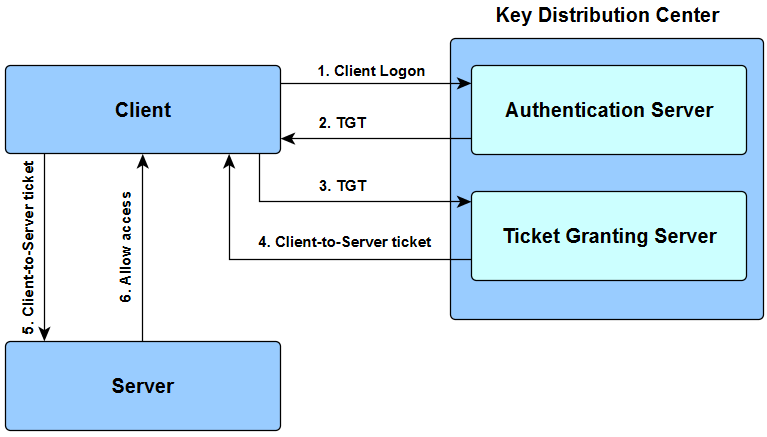
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security

Kerberos Authentication What It Is How It Works Bmc Software Blogs
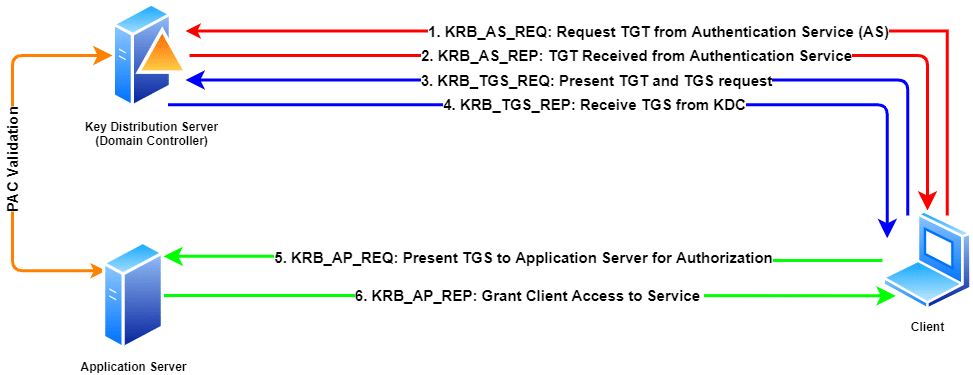
What Is Kerberos Understanding Kerberos What Is It How Does It Work

Kerberos Authentication Explained
The Original Kerberos Authentication Protocol Phase 1 Client Verifies Download Scientific Diagram
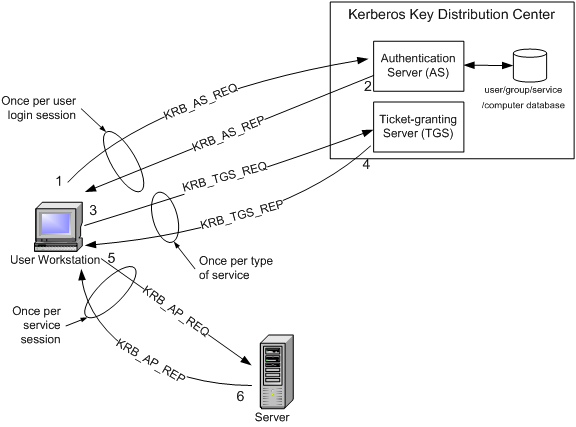
Intel Amt Sdk Implementation And Reference Guide
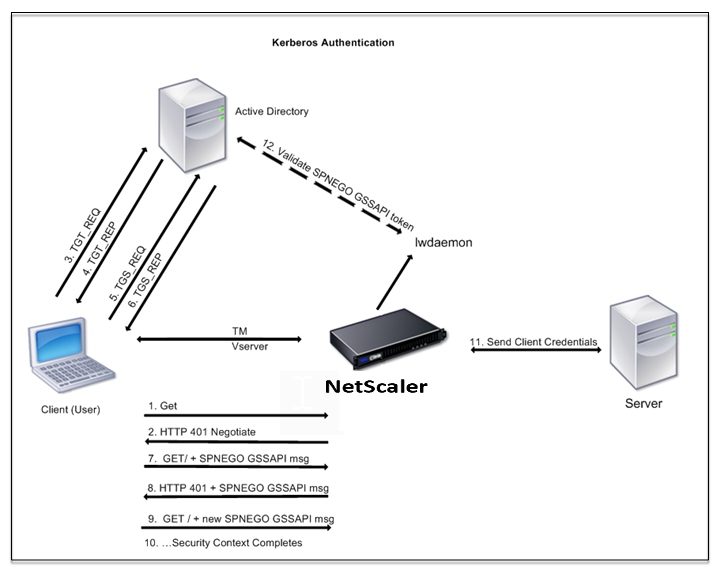
How Citrix Adc Implements Kerberos For Client Authentication

Windows Event Id 4768 A Kerberos Authentication Ticket Was Requested Adaudit Plus